Security & Privacy
How Tetrix AI keeps your code and infrastructure data safe
Your Security is Our Top Priority
At Tetrix AI, we understand that you're trusting us with access to your most valuable assets—your code and infrastructure. We take this responsibility seriously and have built security into every aspect of our platform.
Our commitment to you:
- Enterprise-grade security by design
- Complete data isolation between users
- You maintain full control over your data
- Transparent about what we access and store
- Regular security audits and updates
How We Keep Your Data Safe
End-to-End Encryption
Every piece of data between you and Tetrix is encrypted:
Data in Transit:
- All connections use TLS 1.3 encryption
- Industry-standard SSL certificates
- Encrypted API communications
- Secure WebSocket connections
Data at Rest:
- Encrypted database storage
- Encrypted backups and snapshots
- Industry-standard encryption algorithms (AES-256)
- Secure key management
Your data is encrypted from the moment it leaves your systems until it reaches our secure infrastructure, and remains encrypted while stored.
Complete User Isolation
Your data never mixes with other users' data. Period.
How we ensure isolation:
- Separate database instances per user
- Isolated execution environments for AWS access
- Individual Knowledge Graphs per account
- No shared credentials or access tokens
- Independent security boundaries
What this means for you:
- Other users cannot access your data under any circumstances
- Your code and infrastructure analysis is completely private
- No cross-contamination of any kind
- Each user operates in their own secure environment
You Control Access
You maintain complete control over what Tetrix can access:
Granular Permissions:
- Choose specific repositories to connect
- Select which AWS accounts to integrate
- Revoke access at any time
- Remove individual repositories or accounts
- View all connected services anytime
Easy Disconnection:
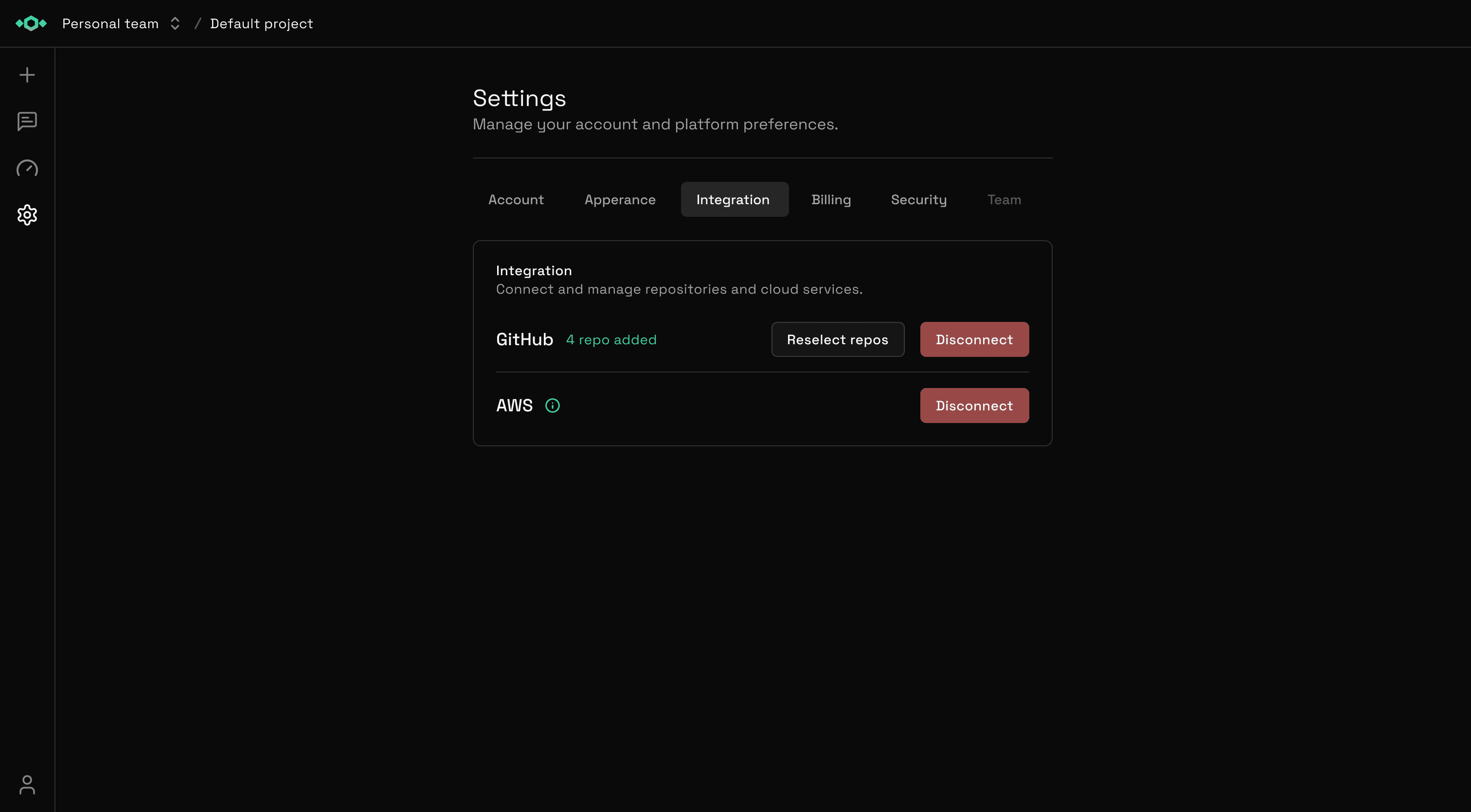
You can disconnect any integration instantly from Settings—no waiting, no approval needed. Your data, your control.
OAuth Security
We use industry-standard OAuth for authentication:
GitHub OAuth:
- Secure, token-based authentication
- No password storage by Tetrix
- Tokens encrypted at rest
- Automatic token refresh
- Revocable at any time from GitHub settings
Google OAuth:
- Secure authentication flow
- No password access
- Minimal profile information
- Easy to revoke
Your GitHub/Google tokens:
- Never exposed in our UI
- Stored encrypted in secure vaults
- Used only for authorized API calls
- Can be revoked by you anytime
What We Access
We believe in transparency. Here's exactly what Tetrix accesses and why:
GitHub Integration
What we access: ✅ Repository structure and organization ✅ Code relationships and dependencies ✅ Function signatures and API endpoints ✅ Configuration files and documentation ✅ Commit metadata (not full history)
What we DON'T access: ❌ Full source code content (only analyzed in memory) ❌ Secrets, API keys, or environment variables ❌ Private data in your repositories ❌ Credentials stored in code ❌ Personal information in commits
Why webhook access? We need to create and manage webhooks to keep your Knowledge Graph updated in real-time. Webhooks notify us of code changes so we can update our analysis automatically—you never need to manually sync.
AWS Integration
What we access: ✅ Resource configurations (EC2, Lambda, RDS, etc.) ✅ Infrastructure topology and relationships ✅ Cost and billing data ✅ Performance metrics from CloudWatch ✅ Security group and IAM policy configurations
What we DON'T access: ❌ Data stored in your databases ❌ Content of S3 buckets ❌ Application logs or sensitive data ❌ Customer information or PII ❌ AWS credentials or secrets ❌ Private keys or certificates
Read-only access: All AWS permissions are read-only. Tetrix cannot create, modify, or delete any AWS resources.
What We Store
We believe in minimal data retention—we only store what's necessary for Tetrix to work effectively.
In Our Knowledge Graph
What we store:
- Code structure and relationships (not full source)
- Function and class signatures
- API endpoint definitions
- Database schema structures
- Infrastructure configurations and relationships
- Analysis metadata and timestamps
What we DON'T store:
- Full source code files
- Proprietary business logic in detail
- Secrets or credentials from your code
- Personal information from commits
- Customer data or PII
- AWS resource data (only configurations)
Temporary Processing
During analysis:
- Code files loaded in memory temporarily
- Analyzed to build relationship graph
- Discarded after processing complete
- Never written to permanent storage
Your source code passes through our analysis pipeline but is never permanently stored. We only keep the structural relationships and metadata needed for intelligent assistance.
Security Architecture
Isolated Execution Environments
When you connect AWS, Tetrix creates a dedicated execution environment for your infrastructure analysis:
Security benefits:
- Your AWS credentials never mix with other users
- Complete computational isolation
- Dedicated resources per user
- No shared execution context
How it works:
- Environment created when you connect AWS
- Operates independently in isolated space
- Destroyed when you disconnect AWS
- Automatic security updates and patching
Secure Credential Management
GitHub Tokens:
- Stored in encrypted vault
- Accessed only during authorized operations
- Rotated automatically by GitHub
- Never logged or exposed
AWS Credentials:
- Temporary credentials only (via IAM role assumption)
- No long-term credential storage
- Credentials expire automatically (typically 1 hour)
- New credentials obtained per session
Your control:
- Revoke GitHub access anytime from GitHub settings
- Delete AWS IAM role to immediately revoke access
- Both methods are instant and effective
Data Privacy
What We Track
We collect minimal analytics to improve Tetrix:
Usage analytics:
- Feature usage (which features you use)
- Error rates and performance metrics
- General query patterns (not query content)
What we DON'T track:
- Specific code or repository details
- Contents of your questions to Tetrix
- Infrastructure configurations
- Personal or sensitive information
Data Retention
Active accounts:
- Knowledge Graph retained while account is active
- Enables fast, accurate responses
- Updated continuously with changes
Deleted accounts:
- All data deleted within 30 days
- No backups retained after deletion
- Complete data removal from all systems
Disconnected integrations:
- Repository data deleted immediately
- AWS data removed within 24 hours
- Can be reconnected anytime
Compliance & Standards
Tetrix adheres to industry best practices and standards:
Security practices:
- Regular security audits
- Penetration testing
- Code security reviews
- Dependency vulnerability scanning
Industry standards:
- SOC 2 Type II compliant (in progress)
- GDPR compliant
- CCPA compliant
- ISO 27001 aligned
Your Control & Rights
Manage Your Data
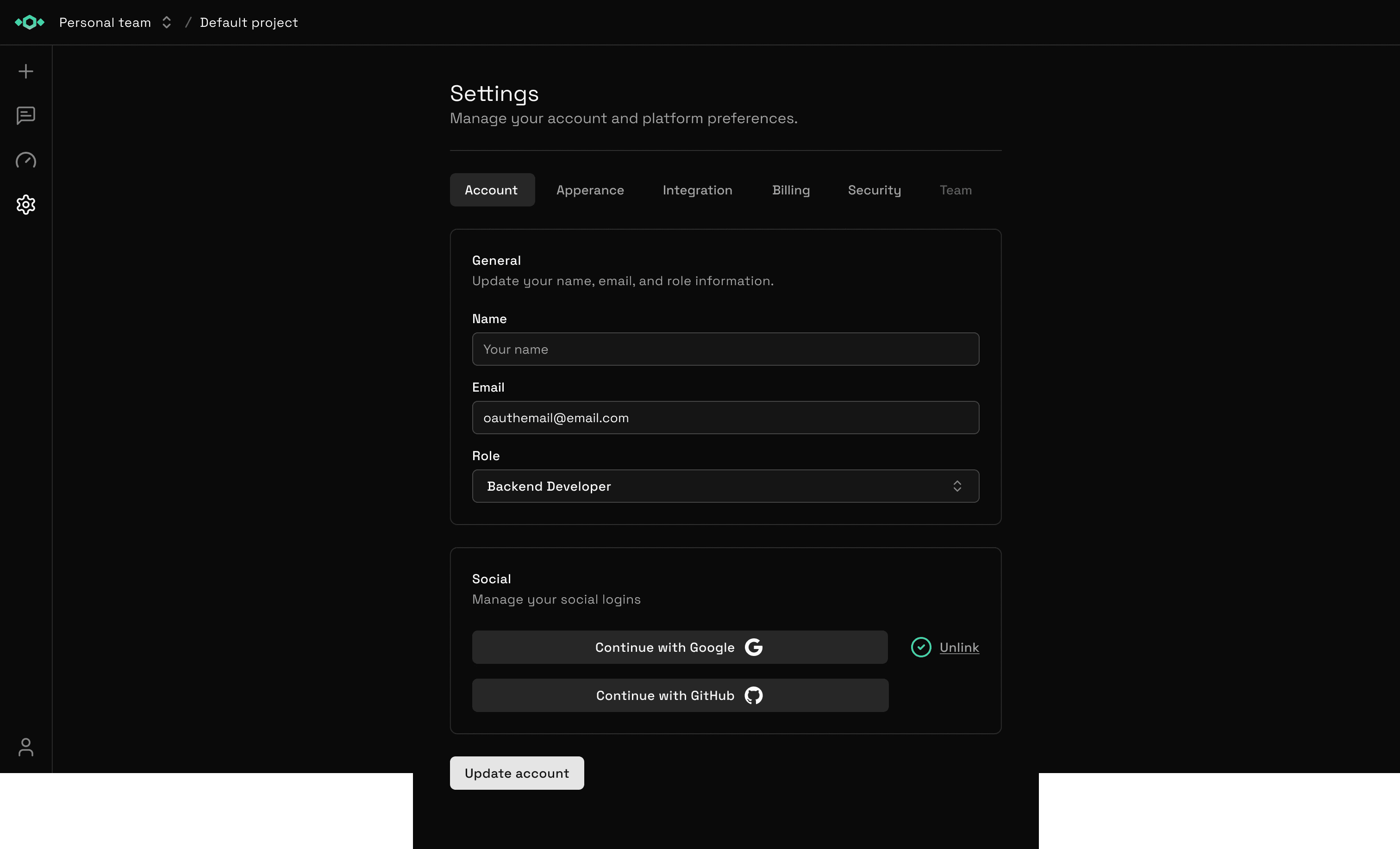
From Settings, you can:
- View all connected integrations
- Disconnect services instantly
- See what data Tetrix has access to
- Export your data (coming soon)
- Delete your account and all data
Revoke Access Anytime
From Tetrix:
- Settings > Integrations > Disconnect
- Immediate effect
- Data removal begins immediately
From External Services:
- GitHub: Settings > Applications > Revoke Tetrix
- Google: Account > Security > Third-party access > Remove Tetrix
- AWS: Delete the IAM role in AWS Console
All methods work instantly—you're always in control.
Data Deletion
Want to delete your account?
- Go to Settings > Account
- Click "Delete Account"
- Confirm your choice
- All data deleted within 30 days
What gets deleted:
- All Knowledge Graph data
- Connection information
- Account details
- Cached analysis results
Data Export
Request your data anytime:
- Email support@tetrix.ai
- We'll provide your data within 30 days
- Includes all stored analysis and metadata
Security Best Practices for Users
Help us keep your account secure:
Strong Authentication
✅ Do:
- Use a strong, unique password
- Enable two-factor authentication (when available)
- Use OAuth when possible
- Keep your email account secure
❌ Don't:
- Reuse passwords from other sites
- Share your Tetrix account credentials
- Use simple or common passwords
Access Management
✅ Do:
- Review connected repositories regularly
- Disconnect unused integrations
- Monitor OAuth applications in GitHub settings
- Check AWS IAM role usage occasionally
❌ Don't:
- Connect repositories you don't need analyzed
- Leave old integrations connected indefinitely
- Ignore security notifications
Repository Security
✅ Do:
- Remove secrets before committing code
- Use GitHub secrets for sensitive data
- Follow security best practices in your repositories
- Regularly audit repository access
❌ Don't:
- Commit API keys or passwords to repositories
- Store credentials in code
- Connect test repositories with fake but realistic-looking secrets
Reporting Security Issues
Found a security concern? We want to know.
Contact us:
- Email: security@tetrix.ai
- Response time: Within 24 hours
- We take all reports seriously
What to include:
- Description of the issue
- Steps to reproduce (if applicable)
- Potential impact
- Your contact information
Our commitment:
- Prompt investigation of all reports
- Keep you informed of progress
- Credit security researchers (if desired)
- Fix verified issues quickly
Transparency & Trust
We believe security through transparency:
Our promises:
- Never sell your data
- Never share data with third parties without consent
- No hidden data collection
- Clear communication about any changes
Questions?
If you have any questions about security or privacy:
- Email: support@tetrix.ai
- Documentation: This page and integration guides
- We're here to help
Regular Updates
Security is an ongoing commitment:
- Regular security patches and updates
- Continuous monitoring for threats
- Proactive security improvements
- Staying current with best practices
We'll notify you of any significant security updates that affect you.
Bottom line: Your code and infrastructure data are safe with Tetrix. We've built security into every layer of our platform, give you complete control, and maintain transparency about our practices. Your trust is our most valuable asset.
Have more questions? Contact us at security@tetrix.ai or support@tetrix.ai