AWS Integration
Connect your AWS infrastructure for comprehensive system analysis and optimization
Overview
The AWS integration extends Tetrix's understanding from your code to your cloud infrastructure. By connecting AWS, Tetrix can:
- Analyze Infrastructure: Understand your EC2, Lambda, RDS, S3, and other AWS resources
- Optimize Costs: Identify expensive resources and suggest cost-saving opportunities
- Improve Security: Analyze IAM policies, security groups, and access patterns
- Map Code to Infrastructure: Understand which services deploy to which resources
- Monitor Resource Usage: Track utilization and identify optimization opportunities
- Consolidated Insights: Answer questions that span both code and infrastructure
AWS integration is optional but highly recommended for teams using AWS. You can add it during onboarding or later from Settings.
Prerequisites
Before connecting AWS, ensure you have:
- An AWS account with appropriate permissions
- Access to create IAM roles in your AWS account
- Understanding of IAM roles and policies (basic knowledge)
- Your AWS Account ID
You'll need IAM permissions to create roles and attach policies. If you don't have these permissions, contact your AWS administrator.
How AWS Integration Works
Secure Architecture
Tetrix uses a secure, isolated architecture for AWS access:
IAM Role-Based Access:
- You create an IAM role in your AWS account
- Tetrix assumes this role using temporary credentials
- No long-term credentials stored
- You control exactly what Tetrix can access
Isolated Environments:
- Each user gets a dedicated, isolated execution environment
- Your AWS credentials never mix with other users
- Complete data isolation and security
- Independent analysis and querying
Read-Only Access:
- Tetrix requests only read permissions
- No ability to create, modify, or delete AWS resources
- Safe, non-invasive infrastructure analysis
Setup Process
Follow these steps to connect your AWS account to Tetrix.
Step 1: Create IAM Policy
First, create a custom IAM policy that grants Tetrix the necessary read permissions.
- Open the AWS IAM Console
- Navigate to Policies in the left sidebar
- Click Create Policy
- Choose the JSON tab
- Paste the following policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:Describe*",
"lambda:List*",
"lambda:Get*",
"rds:Describe*",
"s3:List*",
"s3:GetBucket*",
"dynamodb:List*",
"dynamodb:Describe*",
"ecs:Describe*",
"ecs:List*",
"eks:Describe*",
"eks:List*",
"elasticloadbalancing:Describe*",
"cloudwatch:Get*",
"cloudwatch:List*",
"cloudwatch:Describe*",
"iam:Get*",
"iam:List*",
"ce:Get*",
"ce:Describe*",
"organizations:Describe*",
"organizations:List*"
],
"Resource": "*"
}
]
}- Click Next: Tags (tags are optional)
- Click Next: Review
- Name the policy: TetrixReadOnlyPolicy
- Add a description: "Read-only access for Tetrix AI infrastructure analysis"
- Click Create Policy
This policy grants read-only access to common AWS services. All permissions are view-only—Tetrix cannot modify your infrastructure.
Step 2: Create IAM Role
Now create an IAM role that Tetrix will assume to access your infrastructure.
- In the IAM Console, navigate to Roles
- Click Create Role
- Select AWS Account as the trusted entity type
- Choose Another AWS Account
- Enter Tetrix's AWS Account ID: [Contact support for this ID]
- Check Require external ID for additional security
- Enter External ID: [Contact support for your unique external ID]
- Click Next: Permissions
- Search for and select TetrixReadOnlyPolicy (the policy you just created)
- Click Next: Tags (tags are optional)
- Click Next: Review
- Name the role: TetrixAnalysisRole
- Add a description: "Role for Tetrix AI to analyze AWS infrastructure"
- Click Create Role
Step 3: Copy Role ARN
After creating the role, you need to copy its ARN (Amazon Resource Name) to provide to Tetrix.
- Find TetrixAnalysisRole in your list of IAM roles
- Click on the role name to open its details
- Copy the Role ARN at the top of the page
- It will look like:
arn:aws:iam::123456789012:role/TetrixAnalysisRole
Keep this ARN handy for the next step.
Step 4: Connect to Tetrix
Now connect your AWS account in the Tetrix dashboard.
- Go to Settings > Integrations in Tetrix
- Find the AWS Integration section
- Click Connect AWS
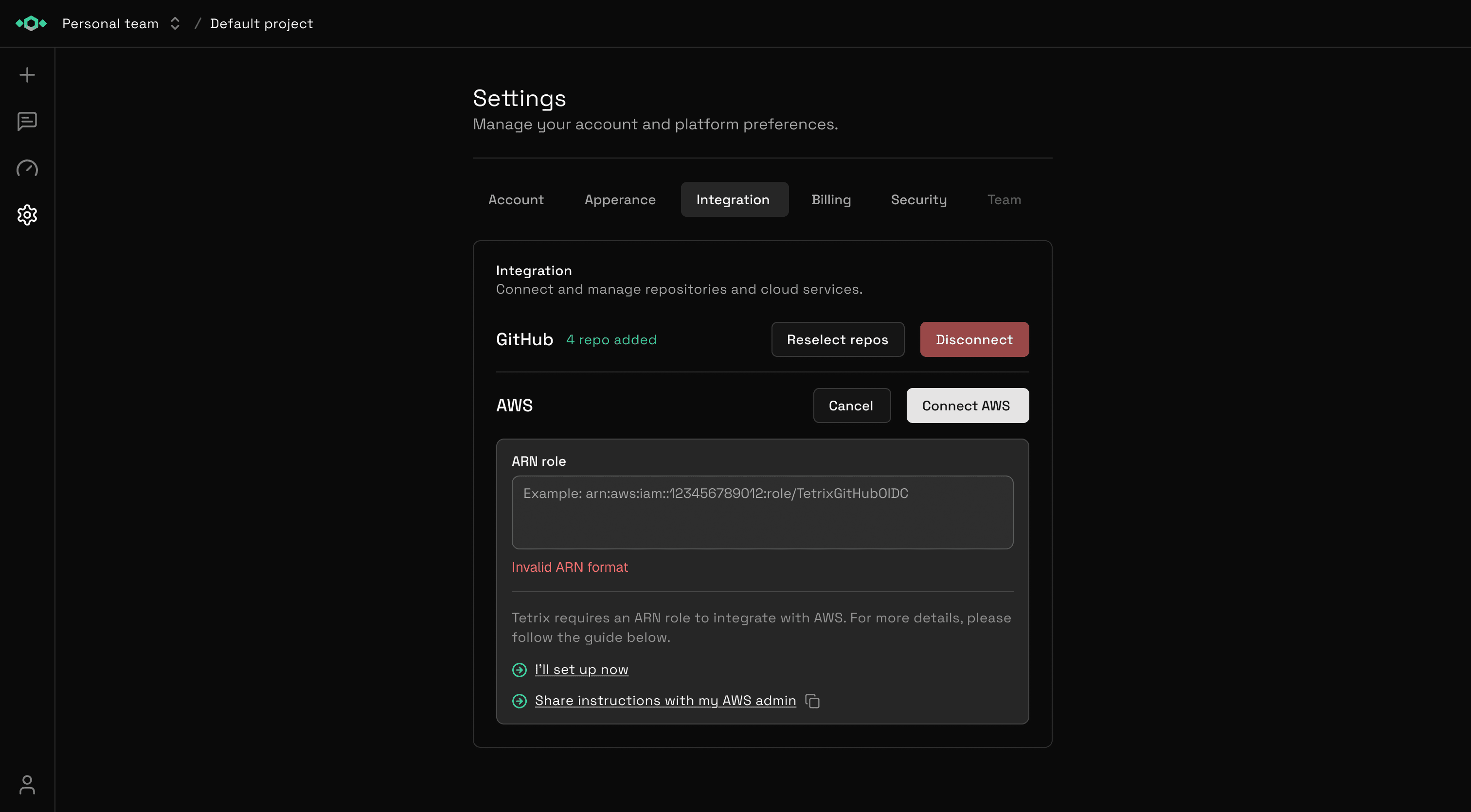
- Paste your Role ARN in the provided field
- Optionally add a friendly name (e.g., "Production Account")
- Click Connect
Step 5: Verify Connection
Tetrix will verify the connection by attempting to assume the IAM role.
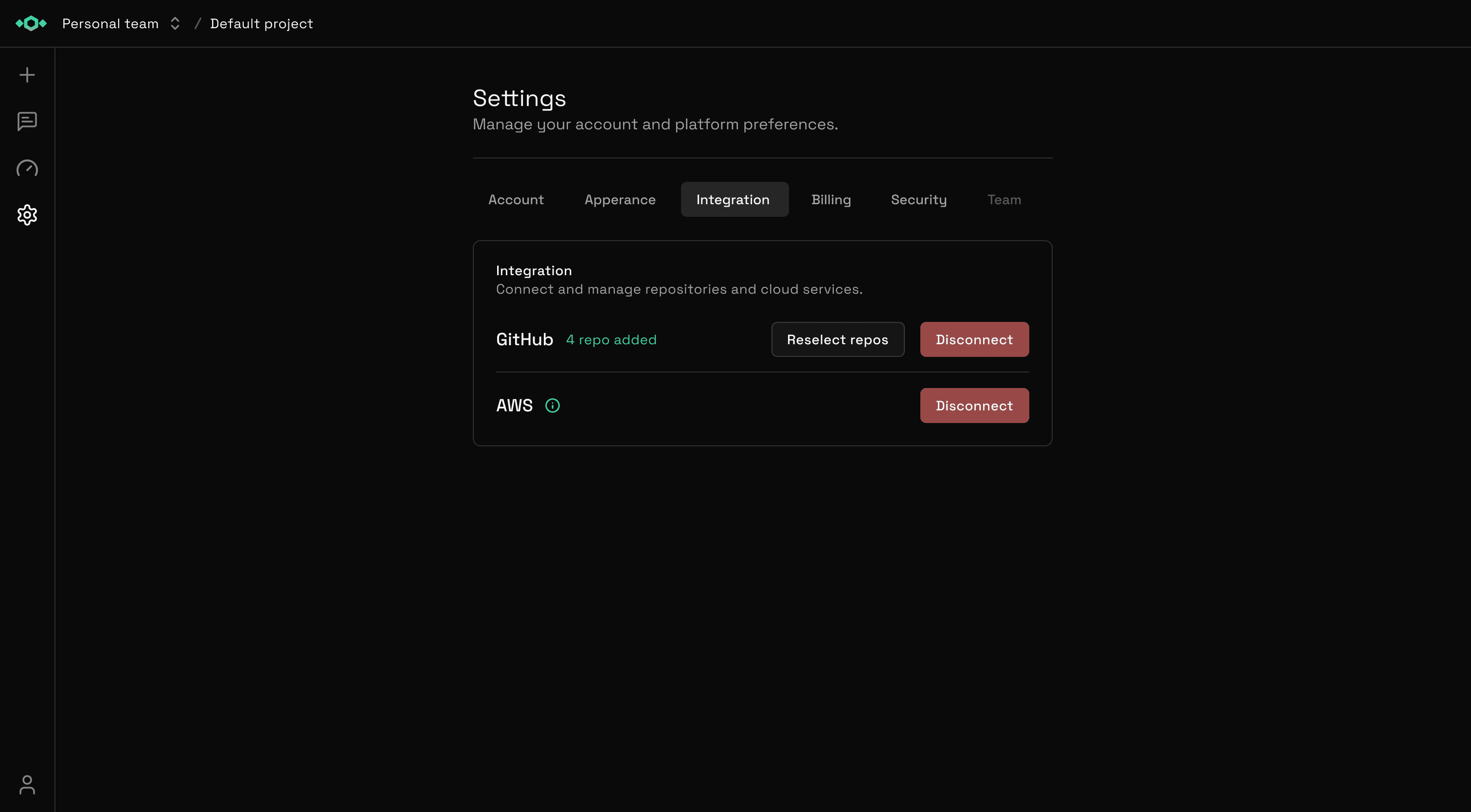
If successful, you'll see:
- ✅ Connection status: Active
- Your AWS Account ID
- Connected timestamp
- List of accessible services
If the connection fails, check:
- Role ARN is correct and copied completely
- Tetrix Account ID is correct in the trust policy
- External ID matches (if used)
- Policy is attached to the role
- Role hasn't been deleted
Step 6: Initial Analysis
Once connected, Tetrix begins analyzing your AWS infrastructure:
- Inventorying all accessible resources
- Mapping relationships between services
- Analyzing cost and usage patterns
- Checking security configurations
- Building the infrastructure portion of your Knowledge Graph
This initial analysis typically takes 5-10 minutes depending on your infrastructure size.
What Tetrix Analyzes
Compute Resources
EC2 Instances:
- Instance types, sizes, and states
- Security groups and network configuration
- Attached volumes and snapshots
- Tags and metadata
- CPU, memory, and network utilization
Lambda Functions:
- Function configurations and runtime
- Environment variables and settings
- Invocation frequency and duration
- Error rates and performance metrics
- Execution role and permissions
ECS/EKS Containers:
- Cluster configurations
- Service definitions and task specs
- Container resource allocation
- Scaling policies and configurations
Data & Storage
RDS Databases:
- Database engines and versions
- Instance sizes and configurations
- Storage types and capacity
- Backup and maintenance settings
- Performance metrics and slow queries
- Security groups and access control
DynamoDB Tables:
- Table configurations and capacity
- Read/write throughput settings
- Global secondary indexes
- Stream configurations
- Item counts and storage size
S3 Buckets:
- Bucket policies and ACLs
- Lifecycle policies
- Versioning and encryption settings
- Storage classes and costs
- Public access configurations
Networking
VPC Configuration:
- VPC and subnet layouts
- Route tables and gateways
- Network ACLs and security groups
- VPN and Direct Connect setups
- Internet and NAT gateways
Load Balancers:
- Application and Network Load Balancers
- Target groups and health checks
- SSL/TLS certificates
- Routing rules and listeners
Security & Access
IAM Analysis:
- Roles, users, and groups
- Policy attachments and permissions
- Access keys and usage
- Service-linked roles
- Permission boundaries
Security Groups:
- Inbound and outbound rules
- Port configurations
- IP whitelists and access patterns
- Unused security groups
Monitoring & Cost
CloudWatch Metrics:
- Resource utilization metrics
- Custom application metrics
- Alarms and thresholds
- Log groups and insights
Cost Explorer Data:
- Current month spending
- Service-level cost breakdown
- Historical cost trends
- Reserved Instance utilization
- Savings Plan coverage
Use Cases
Ask Infrastructure Questions
Resource Inventory:
- "What EC2 instances are currently running?"
- "List all RDS databases and their configurations"
- "Show me all S3 buckets and their access policies"
Configuration Analysis:
- "What security groups are attached to the production database?"
- "Show the VPC configuration for my application"
- "What IAM roles have admin access?"
Cost Optimization
Spending Analysis:
- "What are my most expensive AWS services?"
- "Show me the cost breakdown by service for this month"
- "Which resources are costing more than $100/month?"
Optimization Opportunities:
- "Identify underutilized EC2 instances"
- "Find unused Elastic IPs and volumes"
- "Suggest right-sizing opportunities for my databases"
- "Which Lambda functions are most expensive?"
Security Analysis
Security Posture:
- "Are any S3 buckets publicly accessible?"
- "What security groups allow unrestricted SSH access?"
- "Show me IAM users with admin permissions"
- "Identify security groups with overly permissive rules"
Compliance Checks:
- "Which databases don't have encryption enabled?"
- "Are all EBS volumes encrypted?"
- "Show me resources without proper tags"
Code-to-Infrastructure Mapping
Deployment Understanding:
- "Which Lambda functions are called by the payment service?"
- "What database does the user-service connect to?"
- "Show me the infrastructure for the API Gateway"
- "Map this microservice to its AWS resources"
Multi-Account Support
Tetrix supports multiple AWS accounts, ideal for:
- Development, staging, and production separation
- Multi-region deployments
- Different teams or projects
- Client accounts (for agencies)
Adding Additional Accounts
- Go to Settings > Integrations > AWS
- Click Add Another Account
- Follow the same IAM role creation process for the new account
- Provide the new role ARN
- Give it a descriptive name (e.g., "Dev Account", "Staging")
Benefits:
- Unified view across all environments
- Compare configurations between accounts
- Track costs across multiple accounts
- Environment-specific queries
Querying Multiple Accounts
When you have multiple accounts connected:
"What EC2 instances are running in production?"
"Compare database configurations between dev and prod"
"Show total AWS costs across all accounts"Tetrix understands context and can query specific accounts or aggregate across all of them.
Dynamic Environments
Tetrix uses isolated execution environments for secure AWS access.
How It Works
When you connect AWS, Tetrix creates a dedicated, isolated environment for your account analysis:
Security Benefits:
- Your AWS credentials never mix with other users
- Complete isolation of analysis and data
- No shared execution context
- Independent credential management
What This Means for You:
- Faster, more reliable queries
- No risk of credential exposure
- Automatic environment management
- No configuration needed on your part
The environment is automatically:
- Created when you connect AWS
- Paused during inactivity to save costs
- Resumed when needed for queries
- Destroyed if you disconnect AWS
Troubleshooting
Security & Privacy
Tetrix's AWS integration is designed with security as a top priority:
What We Access
✅ Read-only permissions for infrastructure analysis ✅ Resource configurations and metadata ✅ Performance and cost metrics ✅ Security group and IAM policy settings
What We DON'T Access
❌ Data stored in your databases ❌ Content of S3 buckets ❌ Application secrets or credentials ❌ Private keys or certificates ❌ Customer data or PII
Security Measures
- IAM Role-Based Access: Temporary credentials, no long-term storage
- Isolated Environments: Complete separation between users
- Encrypted Communication: All AWS API calls over TLS
- Audit Logging: Complete logs of all AWS access
- Minimal Permissions: Only read access, never write/delete
- Credential Rotation: Automatic rotation of temporary credentials
Your AWS credentials are never stored permanently. Tetrix only uses temporary session credentials that expire automatically.
Revoking Access
You can revoke Tetrix's access to AWS at any time:
In Tetrix:
- Go to Settings > Integrations > AWS
- Click "Disconnect"
- Confirm the action
In AWS:
- Delete the TetrixAnalysisRole in IAM
- Or modify the trust policy to remove Tetrix's account
Either method immediately revokes access.
Best Practices
IAM Policy Management
✅ Do:
- Use the recommended policy as a starting point
- Add permissions incrementally as needed
- Review and audit IAM policies regularly
- Use external ID for additional security
- Document what each policy grants access to
❌ Don't:
- Grant more permissions than necessary
- Share IAM roles with other services
- Hard-code credentials anywhere
- Skip the external ID validation
Account Organization
✅ Do:
- Use separate accounts for dev/staging/prod
- Give each account connection a clear name
- Document which account is which
- Review connected accounts periodically
❌ Don't:
- Mix production and development in one account connection
- Leave unused account connections active
- Forget to update role names when roles change
Cost Management
✅ Do:
- Regularly review cost optimization suggestions
- Act on recommendations for unused resources
- Monitor spending trends through Tetrix
- Tag resources appropriately for cost tracking
❌ Don't:
- Ignore cost alerts and recommendations
- Leave unused environments connected
- Skip tagging—it makes cost analysis harder
Need Help?
If you encounter issues not covered in this guide:
- Setup Help: support@tetrix.ai
- Security Questions: See our Security page
- IAM Policy Questions: We can provide the latest recommended policy
For urgent connection issues, please include:
- AWS Account ID
- Role ARN (if created)
- Screenshot of any error messages
- When you created the role